Compliance
DORA and identity security: Reducing risk and ensuring digital resilience
As a financial institution or critical ICT third-party service provider, make sure you are ready to meet key DORA compliance requirements with governance and access controls.
DORA now in effect as of 17 January 2025.
Overview
DORA’s framework to protect the financial sector
As financial service institutions such as banks, insurance, and credit card companies grow and transform, so too has their cyber risk. Financial institutions can struggle to manage and secure access to a growing number of identities, which may lead to potential breaches and compliance risk. Additionally, they may face challenges related to legacy systems and the complexity of integrating modern security solutions. The dynamic nature of cyber threats necessitates continuous improvement in Information and Communication Technologies (ICT) risk management to ensure resilience against evolving risks.
The European Union’s (EU) Digital Operational Resilience Act (DORA) provides a comprehensive framework to protect the financial sector from cyber threats through these key pillars:
ICT risk management: Requires financial entities to create an ICT risk management framework, establish protective policies, define roles, implement incident response procedures, conduct regular testing and audits, and manage third-party risks.
ICT-related incident management, classification, and reporting: Mandates financial entities to manage, classify, and report ICT-related incidents, establish early warning indicators, and ensure timely incident reporting to authorities.
Digital operational resilience testing: Requires financial entities to regularly conduct digital operational resilience testing, including threat-led penetration testing, to ensure the robustness of their ICT risk management frameworks.
Managing of ICT third-party risk: Mandates ICT third-party risks through due diligence, monitoring, and ensuring business continuity plans include third-party dependencies.
Information-sharing arrangements: Mandates information-sharing arrangements among financial entities, including sharing cyber threat information, and best practices to enhance collective cyber resilience.
Benefits
Leverage identity security to assist with your DORA Compliance
Identity and access management (IAM) is essential to help achieve DORA compliance by ensuring secure, governed access to ICT systems, thus assisting to mitigating cyber risks, and enhancing the overall digital resilience of financial institutions. Identity security, also known as identity governance, is a pillar of IAM that is crucial to meet key DORA governance and access requirements.
SailPoint Identity Security helps financial institutions and critical ICT third-party service providers become digitally resilient and prepared to meet their requirements in 2025.
By enabling the management and governance of access for every digital identity, financial institutions and critical ICT third-party service providers can:
Enhance ICT risk management
Regular evaluations and vulnerability assessments of identity security measures are crucial for identifying and mitigating potential access-related risks. Leverage SailPoint identity security solutions to help implement a governance model that analyses and manages access related ICT risks effectively.
Detect and report on identity-based anomalies
Strong ICT incident management monitors user activities, detects anomalies, and provides real-time reporting. SailPoint enables you to view historical access data, detect anomalies, remediate risky access, and create real-time reporting. You can also visualise and track governance over time with the Access Intelligence Center.
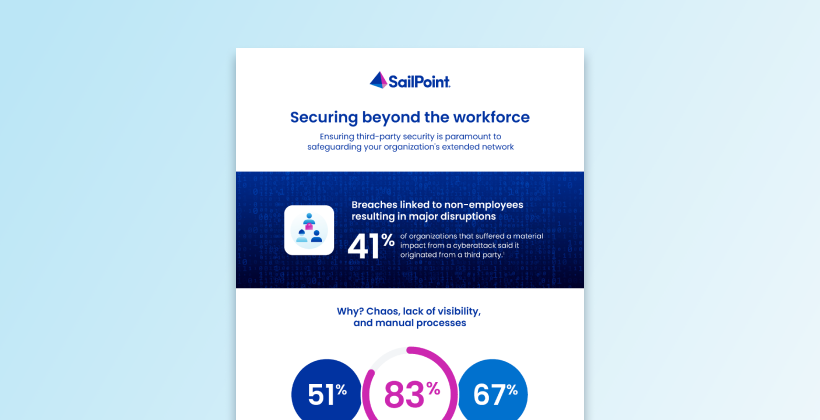
Manage third-party access risk
Third-party risk management and oversight are essential to help prevent unauthorised access. Leverage Non-Employee Risk Management together with the SailPoint Identity Security Cloud to assist with securing your third-party identities via strong management and governance controls.
Secure cloud environments for digital operational resilience
It is critical to implementing effective disaster recovery (DR) and business continuity (BC) strategies to ensure seamless and secure access across cloud services. Cloud Infrastructure Entitlement Management (CIEM) can provide financial institutions with robust access control and management for single and multi-cloud environments.
Safeguard information assets
Safeguard the confidentiality, integrity, and availability of information assets. Data Access Security helps financial entities protect information assets by managing and monitoring access to sensitive data, allowing them to ensure only authorised users have access and assisting to continuously audit access activities.
Customer stories
Leading companies count on SailPoint for identity security
RESOURCES
Learn how SailPoint can help you become DORA compliant
FAQ
Frequently asked questions
What is DORA?
DORA stands for the European Union’s (EU) Digital Operational Resilience Act, which was passed in 2022 to provide a risk management framework with the intention of protecting the EU financial sector from cyber threats. It dictates steps that EU financial institutions must take to protect their information and communication technologies (ICT).
What deadlines are associated with DORA compliance?
Financial institutions and ICT third-party service providers must be prepared to meet their DORA compliance requirements by 17 January 2025.
What entities does DORA apply to?
Article 2 of DORA lists the various types of financial entities falling under its scope: (a) credit institutions;
(b) payment institutions, including payment institutions exempted pursuant to Directive (EU) 2015/2366;
(c) account information service providers;
(d) electronic money institutions, including electronic money institutions exempted pursuant to Directive 2009/110/EC;
(e) investment firms;
(f) crypto-asset service providers and issuers of asset-referenced tokens;
(g) central securities depositories;
(h) central counterparties;
(i) trading venues;
(j) trade repositories;
(k) managers of alternative investment funds;
(l) management companies;
(m) data reporting service providers;
(n) insurance and reinsurance undertakings;
(o) insurance intermediaries, reinsurance intermediaries and ancillary insurance intermediaries;
(p) institutions for occupational retirement provision;
(q) credit rating agencies;
(r) administrators of critical benchmarks;
(s) crowdfunding service providers;
(t) securitisation repositories; and
(u) ICT third-party service providers.
What are the key objectives of DORA?
DORA defines its key pillars to create a comprehensive framework that ensures financial institutions can withstand, respond to, and recover from ICT-related disruptions:
ICT Risk Management
ICT-Related Incident Management, Classification and Reporting
Digital Operational Resilience Testing
Managing of ICT Third-Party Risk
Information-Sharing Arrangements
These pillars are designed to address key areas of operational resilience, from managing ICT risks to ensuring effective incident response and maintaining secure third-party relationships. By standardising practices across these critical areas, DORA aims to enhance the overall stability and security of the EU financial sector.
How does a strong identity security program help meet key DORA compliance requirements?
A mature and strategic identity program must have a governance framework of policies, processes, cultural and technological initiatives, which includes managing an organisation’s users, identities, and access to contribute to a more secure and resilient ICT environment.
Does DORA apply in the United Kingdom since it is out of the EU following Brexit?
DORA applies to UK entities that fall into the following 3 categories:
1. Entities that undertake any of the broad range of financial market activities captured by the Act within the EU
2. Critical ICT Third Party Providers (CTTPS) to Europe’s financial firms
3. Providers not deemed CTTPS under the criteria set out in recently adopted delegate regulations will likely see requirements pushed down the supply chain and built into their contractual relationships with financial firms.
Businesses that operate in the UK only, or in the UK and other non-EU markets, should be aware of the requirements of the UK’s Operational Resilience Framework being developed by the Bank of England, and which are intended to be as interoperable as reasonably practicable with the EU’s DORA.
*DISCLAIMER: THE INFORMATION CONTAINED IN THIS WEBPAGE AND ANY ASSOCIATED INFORMATION CONVEYED IN THE DOCUMENT’S HYPERLINKS IS FOR INFORMATIONAL PURPOSES ONLY, AND NOTHING IN THIS DOCUMENT IS INTENDED TO CONSTITUTE LEGAL ADVICE. SAILPOINT CANNOT GIVE SUCH ADVICE AND RECOMMENDS THAT YOU CONTACT LEGAL COUNSEL REGARDING APPLICABLE LEGAL ISSUES.
Get Started
See why SailPoint identity security is key to assisting with DORA compliance
Discover how our solutions enable financial entities to meet the challenge of ensuring secure access to resources without compromising productivity or innovation.