DATA ACCESS SECURITY
Secure data access for all identities
Govern and secure access to sensitive data for humans and machines. Enable a secure, AI-powered business.
Challenge & solution
Identity-first data access
Enterprise data is growing fast — and so are access risks from employees, bots, and workplace AI. Many organizations lack the proper visibility to govern data access, leaving risky gaps in compliance and control. SailPoint Data Access Security extends identity security and access controls to data, securing access across every identity — human or machine.
Govern data access with identity intelligence
Discover, classify, and label sensitive data automatically
Enrich access context with actionable data insights
Enforce least-privilege policies for all identities
Monitor data access and trigger alerts on suspicious activity
Expedite compliance efforts and streamline certifications

SOLUTION BRIEF
Data Access Security use cases
See how SailPoint helps organizations reduce risky data access, enforce least privilege, and protect sensitive information. Explore key use cases and capabilities in this solution brief.
Use cases
Data access governance with identity at the core
Extend intelligent data access governance to your most sensitive data. Ensure only the right identities – human or machine – can access your critical information. Secure data starts with connecting the right identities to the right data.
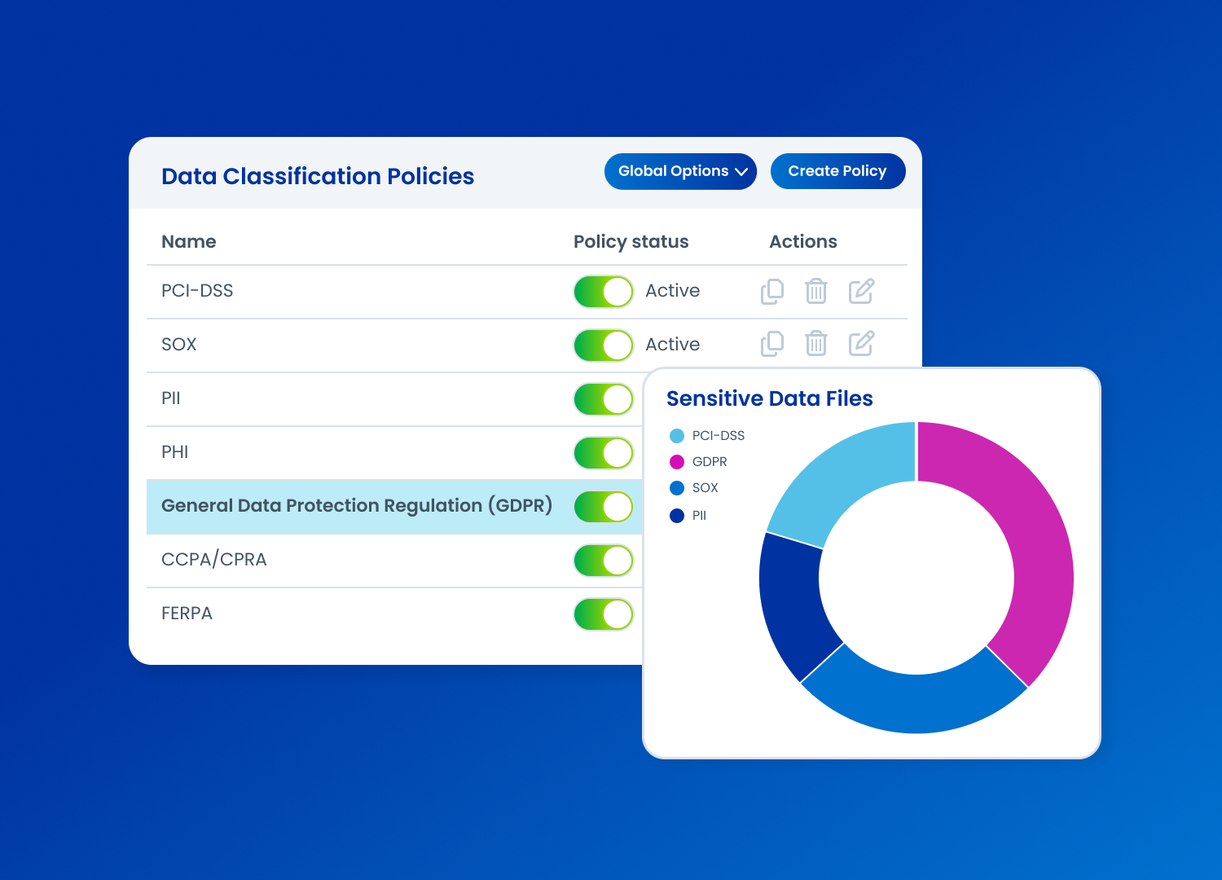
Discover and classify sensitive data
Data Access Security’s automated data discovery and classification capabilities identify sensitive content across your environment — from personal data and financial records to intellectual property. Apply consistent labels, reduce false positives, and streamline enforcement of data access policies at scale across cloud, on-prem, and SaaS environments.
- Automatically classify sensitive data
- Apply consistent tagging and sensitivity labels
- Integrate third-party data classification tags
- Reduce manual effort with dynamic and customizable policies
Govern and secure sensitive data
Excessive permissions and over-permissive access pose a constant risk. With Data Access Security and Identity Security Cloud, you can uncover exposed data — including files shared publicly and elevated privileges — and take fast action to restrict access. Automatically right-size data access and limit blast radius based on roles, usage, and customizable policy.
- Proactively identify over-privileged access
- Detect externally shared sensitive content
- Remove defunct accounts with sensitive access
- Enforce least-privilege policies for every identity
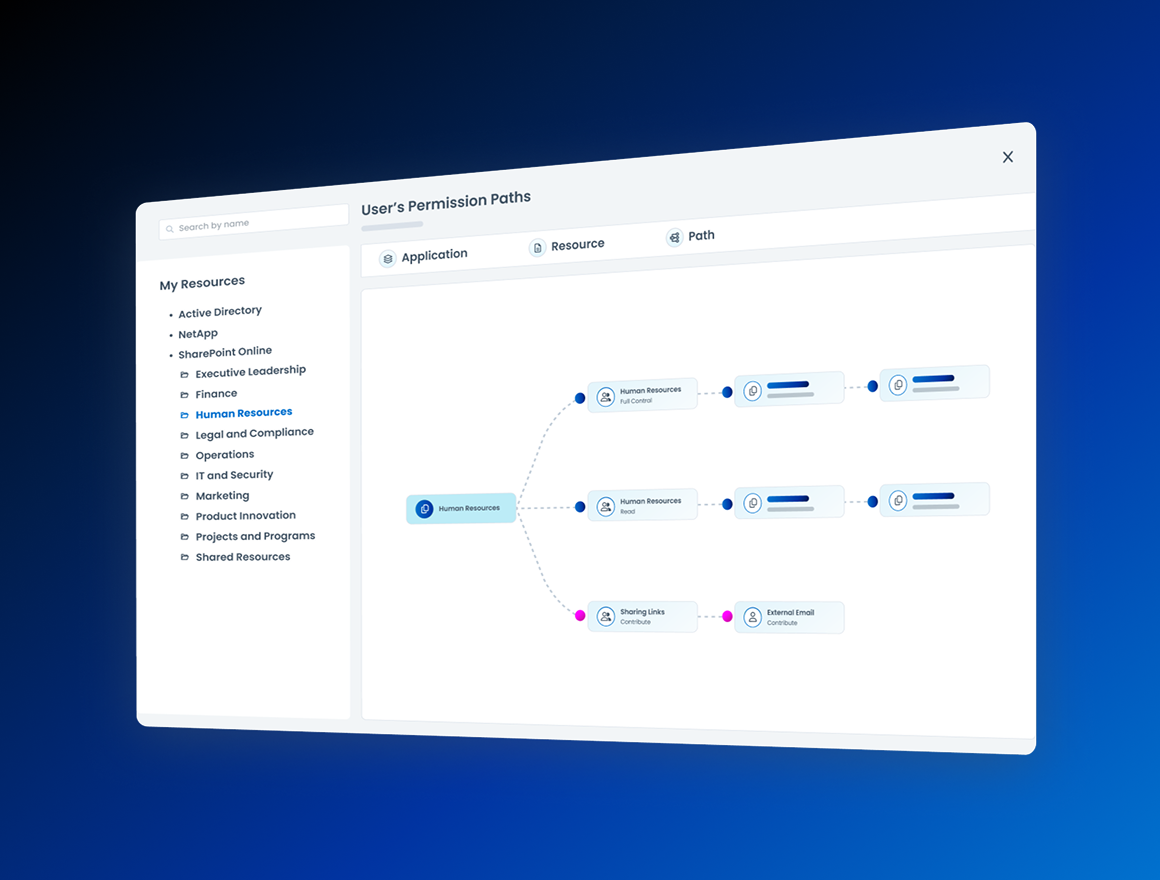

Accelerate compliance readiness
Traditional certifications lack context. Data Access Security adds data-centric risk insight to SailPoint access certifications — showing who accessed what data, how often, and why. Use it to prioritize high-risk access, automate data owner reviews, and prove compliance with confidence.
- Highlight regulated or high-risk entitlements
- Streamline certifications with rich data context
- Enrich certifications with access metadata
- Enable fine-grained access reviews to data assets
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourRelated resources
Data Access Security resources
Start your identity security journey today
SailPoint Identity Security Cloud empowers organizations to intelligently manage and secure real-time access to critical data and applications.
Advanced capabilities
Take your identity security solution even further
SailPoint Identity Security Cloud goes beyond the basics to tackle complex identity challenges. These specialized, add-on solutions offer even greater control and intelligence for reducing risk and ensuring compliance.
Related industries
Data Access Security by industry
Explore how SailPoint helps industry leaders govern access to sensitive data, meet compliance requirements, and reduce risk.
Financial services
Govern access to financial data to help protect against insider threats and regulatory fines.
Learn moreHealthcare
Improve patient data protection, reduce access risk, and support HIPAA compliance with SailPoint.
Learn moreManufacturing
Help Safeguard proprietary designs by controlling access to operational and supplier data.
Learn morefaq
SailPoint Data Access Security FAQ
What is data access governance?
Data access governance is the practice of controlling and monitoring who has access to data across an organization. It ensures only authorized users — including employees, bots, contractors, and AI agents — can access sensitive or regulated information. This improves security, supports compliance, and reduces the risk of data breaches.
How does SailPoint help with data access governance?
SailPoint Data Access Security extends identity governance to sensitive data by discovering where critical information lives, classifying it, and enforcing least-privilege access policies. It connects data access decisions to identity context, enabling smarter, more secure governance across all identities — human and machine.
What types of data can SailPoint discover and classify?
SailPoint can automatically discover and classify a wide range of sensitive data, including PII, financial records, intellectual property, and regulated content across cloud, hybrid, and on-prem environments. It also supports importing existing classification tags, document classification, classification rules, and policies from other tools and vendors.
Why is data access security important for identity programs?
Data is often a blind spot in traditional identity programs. SailPoint bridges that gap by tying identity security directly to data access. This helps organizations enforce zero trust, prevent data overexposure, and align access decisions with real-time data risk.
Can SailPoint monitor and alert on suspicious data access?
Yes. SailPoint provides monitoring and alerting for sensitive data. It detects risky behavior such as unauthorized downloads, off-hours access, and external file sharing, and automatically triggers alerts or remediation workflows to reduce risk quickly.
Can SailPoint control access to overexposed or sensitive data?
Yes. SailPoint helps identify overexposed, misclassified, or sensitive data and can apply least-privilege access policies. It detects excessive permissions, public sharing, and orphaned accounts — allowing organizations to reduce risk and enforce data access controls effectively.
How does SailPoint support data compliance and audits?
SailPoint maintains detailed records of data access and classification to support compliance with regulations like GDPR, HIPAA, SOX, and NIST. It streamlines certifications and provides audit-ready reporting, helping teams meet requirements faster and with less manual labor.
Contact us
Put identity security at the core of securing your business


