Cloud Infrastructure Entitlement Management
Simplifying cloud governance
Extend identity security to cloud infrastructure and govern cloud entitlements

Challenge & solution
Managing complex cloud access
As your organization moves to the cloud, managing who has access to what becomes increasingly complex. Traditional tools weren't built for cloud-native environments, leading to over-privileged access, security gaps, and compliance risks.
Simplifying cloud access and entitlements
Gain unified visibility into all cloud access from a single pane of glass.
Discover and secure all human and non-human identities across multi-cloud environments.
Right-size permissions and enforce least-privilege access with AI-driven insights.

Analyst Report
2025 KuppingerCole Report: Cloud Infrastructure Entitlement Management
Traditional IAM tools often fall short in dynamic, cloud-native environments. Get expert insights to managing cloud access risk effectively in the latest KuppingerCole Leadership Compass Report.
Use cases
Extend identity security to cloud infrastructure
Govern and manage multi-cloud infrastructure with a single approach. Apply clearly defined policies and automate the lifecycle management of IaaS access. By centralizing the management of cloud entitlements, enterprises can reduce administrative overhead and increase operational efficiency. The solution also enhances compliance by offering detailed logging and audit trails, which are crucial for meeting regulatory requirements. Furthermore, the unified approach to identity security across multi-cloud environments simplifies the integration of new cloud services, enabling seamless scalability as business needs grow.
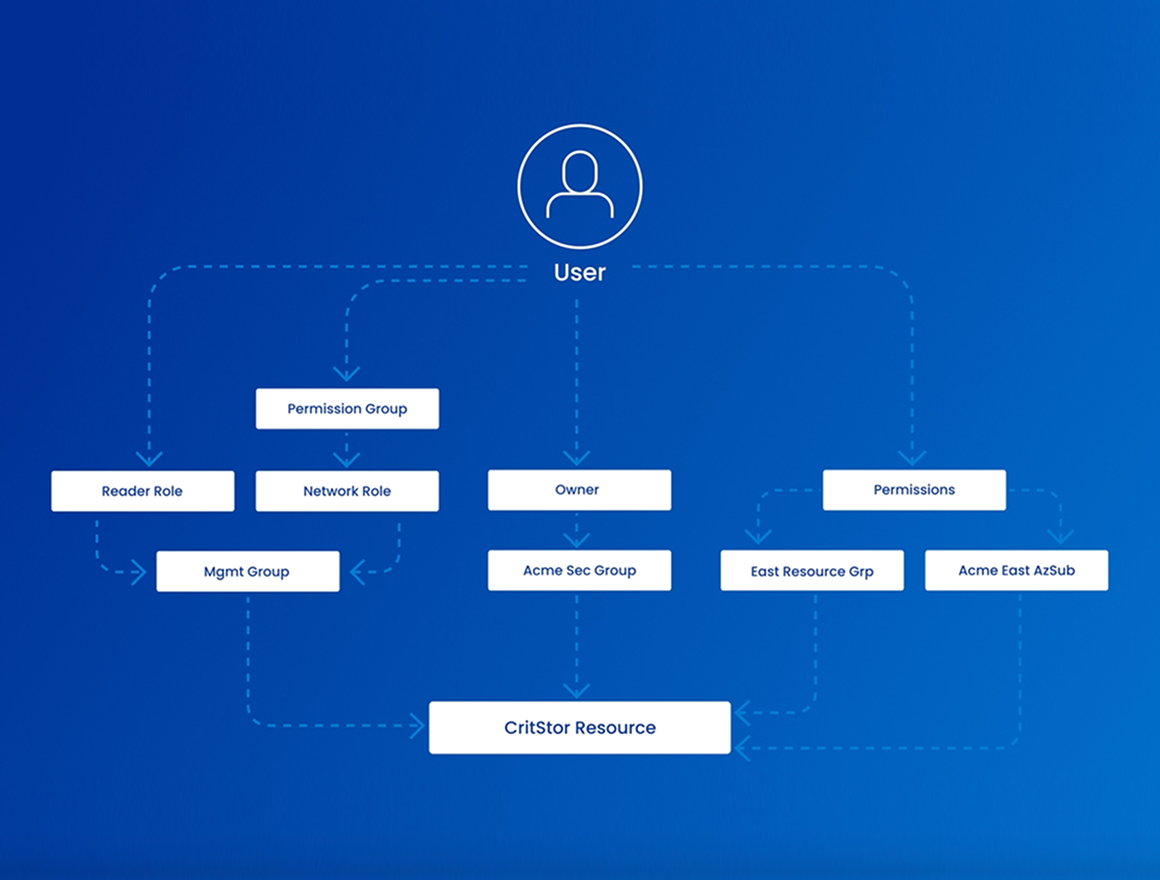
Discover access across complex IaaS environments
Gain a comprehensive, visual map of how identities are connected to cloud resources across your IaaS environments. See entitlements, roles, and access paths in a single graphical view to uncover hidden risks, streamline investigations, and ensure the right people have the right access—no matter how complex the environment.
Tailor policies for optimal security
Adapt your password policies to optimize the security of your enterprise. Customize password complexity, history, and expiration rules for different user populations or application risk levels for a flexible solution.
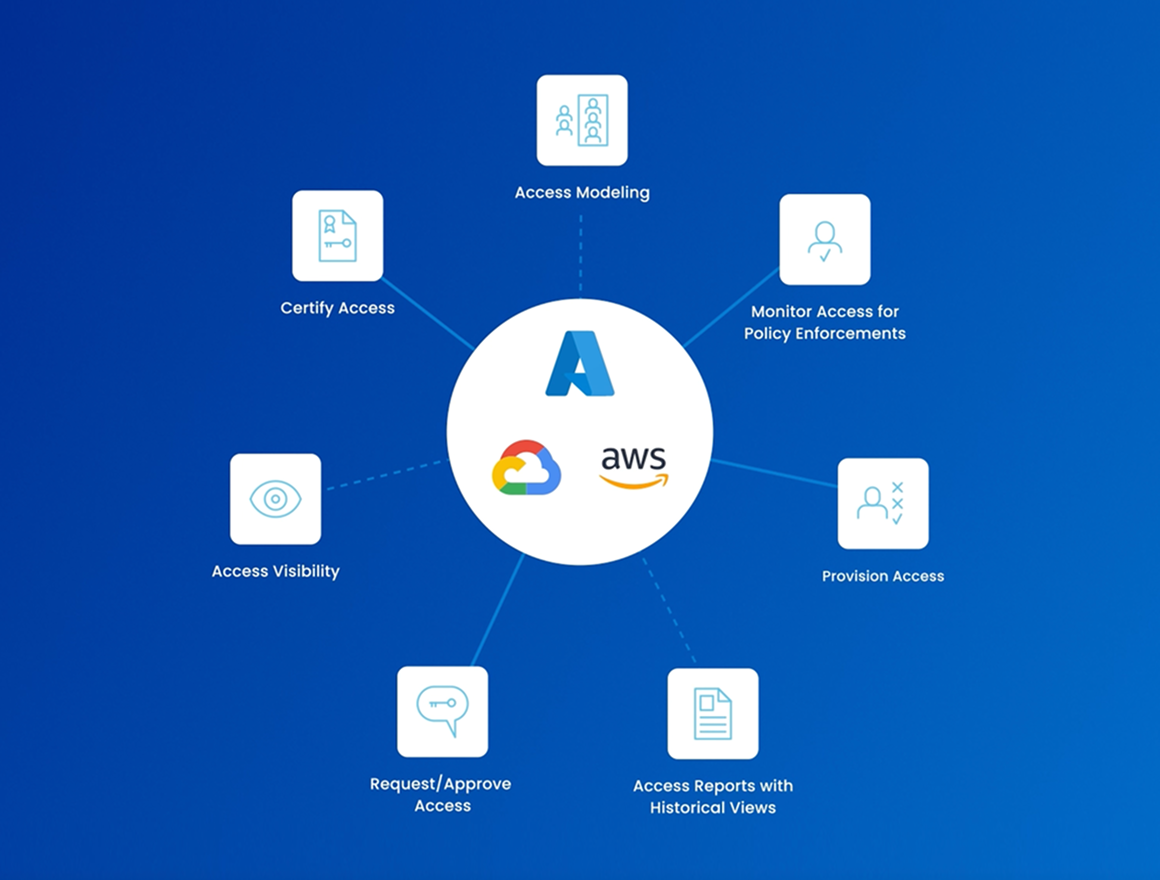
Report and audit cloud infrastructure access
Easily generate audit-ready reports that show who has access to what across your cloud infrastructure. Launch cloud-specific access certification campaigns to review and validate entitlements, helping you meet regulatory requirements, strengthen governance, and prove that your cloud access controls are consistently enforced and well-documented.
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourRelated resources
More about identity security & cloud infrastructure
Start your identity security journey today
SailPoint Identity Security Cloud empowers organizations to intelligently manage and secure real-time access to critical data and applications.
Advanced capabilities
Take your identity security solution even further
SailPoint Identity Security Cloud goes beyond the basics to tackle complex identity challenges. These specialized, add-on solutions offer even greater control and intelligence for reducing risk and ensuring compliance.
faq
Learn more about CIEM
What is the difference between IAM and CIEM?
Identity and Access Management (IAM) and Cloud Infrastructure Entitlement Management (CIEM) are both crucial for safeguarding sensitive data and digital assets, and they serve distinct purposes within the realm of identity security. IAM solutions are designed to manage identities and control access across an organization’s entire IT environment, including applications, data, and services. IAM typically focuses on managing user identities and entitlements to ensure the right individuals have appropriate access to the right resources. Conversely, CIEM specifically addresses the complex nature of cloud infrastructure, which often involves intricate entitlements and varied access levels to numerous cloud resources. CIEM solutions like SailPoint’s Cloud Infrastructure Entitlement Management enhances IAM capability by simplifying the management of cloud infrastructure by revealing what the cloud resources and what specific actions (read, write, or admin) a user can perform so IAM teams can build a robust and secure cloud access model. Whereas IAM offers a broad scope of identity protection, CIEM delves deeper into cloud ecosystems to provide fine-grained control and visibility in multi-cloud environments, thereby significantly enhancing enterprise security postures and removing unnecessary and over privileged access.
What is the difference between CSPM and CIEM?
Cloud Security Posture Management (CSPM) and Cloud Infrastructure Entitlement Management (CIEM) are both crucial for safeguarding cloud infrastructure. CSPM solutions help secure the cloud infrastructure configuration – and help highlight misconfiguration. CSPM focuses on the security policy applied to the cloud infrastructure resource. CIEM focuses on Identity Security. CIEM helps ensure any identity has only the appropriate access. Only tools like ISC with CIEM can help detect if someone in accounting has cloud access. This rich data of what identity – not just a cloud “user” has access to - is the benefit of complimenting CSPM tools with CIEM.
What is the difference between CIEM and SIEM?
Cloud Infrastructure Entitlement Management (CIEM) and Security Information and Event Management (SIEM) likewise serve different purposes in cybersecurity and identity management. CIEM focuses on managing and securing cloud infrastructure entitlements, ensuring the right identities have appropriate access to specific cloud resources and actions such as read, write, or admin permissions. CIEM provides a governance framework that helps businesses secure cloud infrastructure access, similarly to how they manage access to other applications and data. On the other hand, SIEM is designed to monitor, detect and respond to security events and incidents across an organization’s IT environment by collecting and analyzing data from various sources. While CIEM is primarily concerned with entitlement and access control within cloud environments, SIEM aims to provide real-time analysis and event correlation to identify potential security threats and ensure compliance. Combining CIEM and SIEM solutions can provide a comprehensive security posture, bringing together robust access management and vigilant security monitoring.
What is the difference between CIEM and CIAM?
Cloud Infrastructure Entitlement Management (CIEM) and Cloud Identity and Access Management (CIAM) are both fundamental to maintaining secure and controlled access within cloud environments, but they too serve distinct purposes. CIEM focuses specifically on managing the entitlements associated with cloud infrastructure resources, ensuring that the right identities have appropriate access permissions (read, write, admin) to specific cloud resources. This is critical in a multi-cloud environment where granular control over varied infrastructure resources is required to maintainleast privilege. CIAM, however, is primarily concerned with managing and securing user identities and access across cloud applications and services, ensuring that users, such as customers, have secure and seamless access to the organization's cloud-based services. While CIAM secures access to cloud and cloud applications, CIEM drills down into the details of infrastructure access and grants the 'appropriate' access/granular access to the cloud resources used to build and maintain cloud solutions thus providing a finer level of control over who can do what within the cloud infrastructure. This differentiation allows enterprises to precisely tailor their identity security strategies to cover distinct facets of their cloud operations efficiently.
Is Cloud Infrastructure Entitlement Management an add-on to Identity Security Cloud?
Cloud Infrastructure Entitlement Management is included in our Business Plus suite and available as an add-on to the Standard and Business suites of the Identity Security Cloud. This feature gives enterprises the functionality for governing and managing multi-cloud infrastructure.
Contact us
Put identity security at the core of securing your business


