Identity Security Maturity Assessment
Is your program keeping pace?
Take a 6-question checkup to see where your identity program stands today and get prioritized next steps you can act on.
Finish in minutes—no prep required
Get your maturity score instantly
Discover key focus areas for improvement
Share the concise summary with stakeholders
1. Is your identity security strategy understood & utilized across your organization & aligned to your overall business strategy?
Why take the assessment
Establish your baseline
Clarity beats guesswork. This assessment maps your program to the Horizons model. Uncover where you lag behind, align stakeholders on a plan to move forward, and focus investment where it reduces risk most.
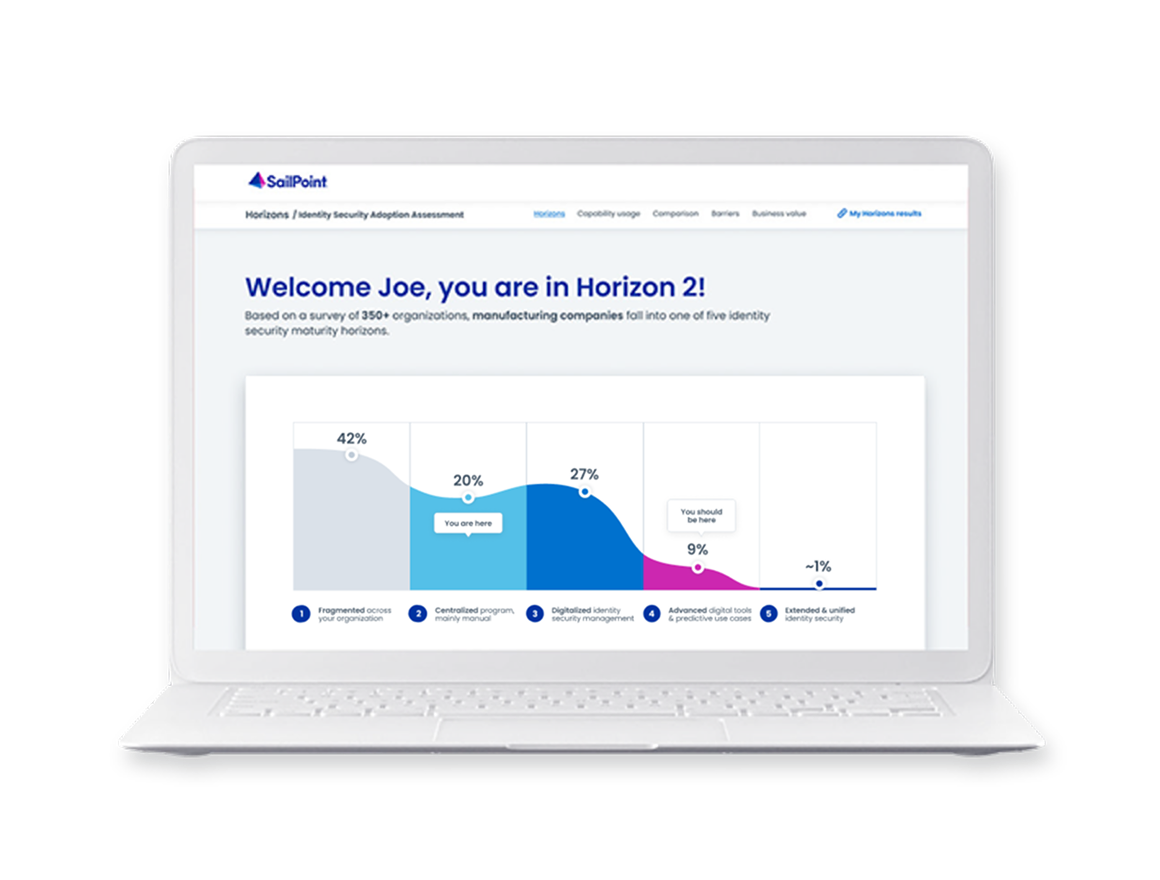
Understanding the Horizons of Identity Security
The Horizons framework reveals how effectively access is governed for every identity—human and machine—across your enterprise. It is based on global research that shows companies typically map to one of five horizons, from fragmented to extended and unified.
At Horizon 1, the lowest maturity, organizations lack the strategy and technology to enable digital identities
Those at Horizon 2 have adopted some identity technology but still rely heavily on manual processes
At Horizon 3 organizations have adopted identity capabilities at scale but with static, rule-based controls
Organizations at Horizon 4 have automated capabilities at scale and use AI to enhance digital identities
Horizon 5, the closest to the future of identity, boundaries are blurred between enterprise identity controls and the external identity ecosystem
How we assess maturity
Pillars of a strong identity security program
Your results are based on four criteria: strategy, operating model, talent, and technology. Each question maps to these criteria to determine your horizon level and highlight strengths, gaps, and the most effective next steps for reducing risk and scaling with confidence.
Strategy
Understood and aligned
Assesses whether an organization-wide identity strategy exists, is understood and used, and aligns to business priorities—from no strategy to very strong. Signals include funding, measurable outcomes, and how identity enables transformation, innovation, and resilience.
