Solution brief
Get More Connected and More Protected with Extensibility
Like many organizations you’ve had to accelerate your business modernization efforts to keep up with today’s fast-changing landscape. This means having to support a growing virtual workforce, adopting cloud infrastructure and applications, and putting a greater focus on security. On top of this digital transformation you must figure out how to maintain the right level of visibility and control across your growing volume and variety of users, applications, data and access.
You likely understand the importance of identity, and may already have some level of automation and business processes in place for your core set of applications and data. But as you continue to modernize your business there are many peripheral identity-related processes that occur both downstream and upstream of your core identity framework. These processes could include logging an identity event into your Amazon CloudWatch application monitoring service, creating a recurring ServiceNow ticket to remove inactive accounts on systems external to your identity solution, or proactively notifying your security team via Slack of critical updates that impact other security-related activities. In many cases these types of processes are either done manually with a team of IT resources, or require significant complex coding to develop and manage them. As the footprint of your users, applications and points of access expand, relying on this approach simply cannot scale. This creates a growing friction that slows down business while opening up a window of security and compliance risk that’s just too great in today’s cyber world. The gaps and blind spots to excess and unauthorized access can easily lead to toxic combinations of access and data loss.
Manual Processes are Costing Your Organization
Regardless, many organizations continue with their legacy, manual or quasi-automated script-driven approach to managing user access. Let’s take a look at how the costs with your current approach can quickly add up even for a simple manual process.
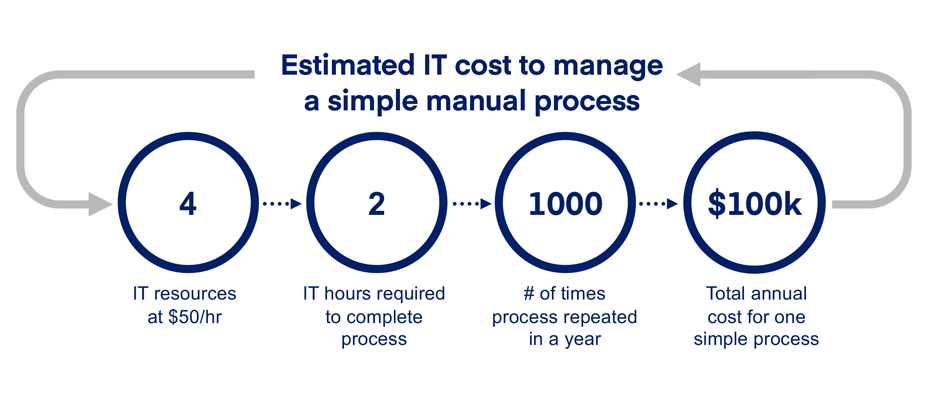
Now imagine if you were managing over 20 concurrent processes, that would be more than $2,000,000 per year. Inevitably your processes would be much more complex, requiring more IT resources and incurring much more cost. Based on this simplified example continuing with your current approach very likely will impact your operational efficiency and productivity but may also put you on the wrong end of data breach. Since the onset of the pandemic, IT workers have reported a 62% increase in ticket volume1. Already taxed by manual processes IT will be slower to respond to potential access and security issues.
You Can’t Outrun Risk with Yesterday’s Approach
As your digital ecosystem continues to expand so too will the accompanying business workflows. If you continue down your current path you will have to bring on additional IT resources in an attempt to keep up. At some point you can only accommodate so many IT resources before it becomes too costly, or the team cannot scale and stay in stride with the business. What if your organization was put at risk from a delay in notifying your security team, or an inactive account that enabled a bad actor to gain access to your environment because of the lack of automation? If your workflows and business processes cannot operate at the speed of business you’re inviting exactly this type of risk. With over 50% of companies experiencing a breach during the pandemic2 and 64% of breaches related to negligence3, at some point these vulnerabilities are likely to become a reality. Explaining the loss of intellectual property, incurred compliance fines, and impact to company value due to a lack of proper and secure automation is not a scenario that is wished upon by anyone.
A New Way Forward with Automation
What if you could get control of your complex ecosystem of applications and business processes by replacing your traditional manual processes with automated workflows? These workflows would not be created with your typical code-heavy development, but instead would leverage API’s and event triggers to build low to no-code workflows that are tailored to your business. No longer do organizations have to rely on inefficient manual intervention from multiple IT resources, instead they can integrate and embed identity to fit their unique set of applications and systems. With the ability to quickly build custom workflows and application integrations companies enable enormous operational efficiency gains, stronger security, and make worker’s lives easier.
Automate Identity-driven Processes with Extensibility
All of this is possible today with the power and extensibility of SailPoint’s Identity Platform. The extensibility framework built into SailPoint’s Identity Platform provides a toolkit of API’s and event triggers to quickly and seamlessly integrate identity security into your existing business processes and ecosystem of applications. Using these API’s and event triggers organizations can rapidly build automated workflows with little to no code. SailPoint’s extensibility framework easily integrates with industry leading iPaaS providers such as Workato and Zapier. It’s now possible to easily incorporate identity into the applications that users rely upon everyday including Slack and Microsoft Teams. Workers can now request access to an application, or approve access right within these collaboration tools, and eliminating the continuous distraction of switching between multiples apps to get your work done. You can increase productivity and efficiency by making it easy for workers to get access and keep working. This also takes the burden off IT and enables them to focus on more strategic initiatives. These extensibility capabilities make your organization more connected and in turn–more protected. You’ll gain deeper insights and control of user access lifecycles and trigger automated processes where once an entire team was needed for manual processing. The possibilities that extensibility provides are limitless, and together with the SailPoint Identity Platform you can take control and embed identity within your digital ecosystem.
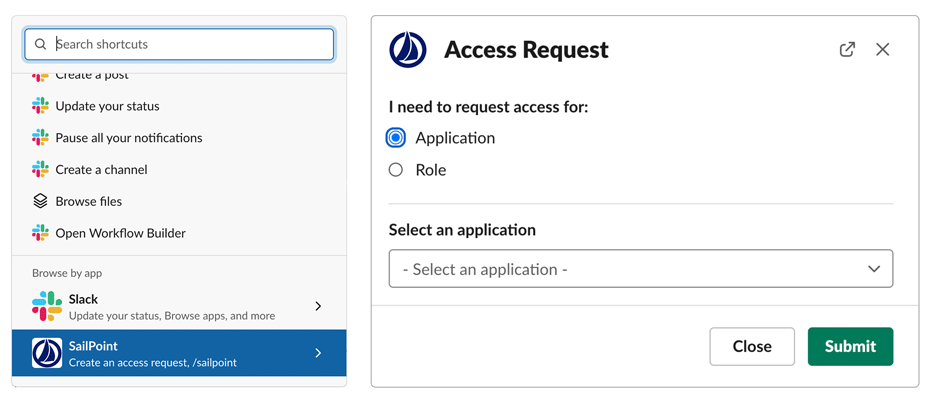
Access request in Slack: Workers can now click on the Slack shortcut button to quickly request access.
Learn more about the SailPoint Identity Platform and API’s and event triggers.


